Understanding cybersecurity maturity models
A comprehensive guide to cybersecurity maturity models such as CMMC, NIST CSF, and C2M2, and how they can strengthen your security posture.

If you're like most IT leaders, you probably find yourself thinking about cybersecurity more than you'd like to admit. New threats pop up daily, regulations keep changing, and your security stack feels like it's always playing catch-up. Sound familiar?
Here's the thing: you don't have to feel like you're constantly reacting to the latest crisis. A cybersecurity maturity model can help you take control by showing you exactly where you stand today and what your next smart move should be.
What is a cybersecurity maturity model?
Think of a cybersecurity maturity model as your security roadmap. It's a practical framework that helps you measure how well your security program is working right now and gives you a clear path to make it stronger.
The beauty of these models is that they take the guesswork out of security planning. Instead of wondering "Are we doing enough?" or scrambling when something goes wrong, you get a structured way to spot gaps, set priorities, and track your progress over time.
Why should you care? Because these models give you something every security team needs: a common language for talking about risk and progress. When you can show leadership exactly where you are and where you're headed, budget conversations get easier. Your team gets clear goals to work toward. And you can finally feel confident that your security investments are actually moving the needle.
Overview of leading cybersecurity maturity models
If you’re exploring ways to improve your security, you’ll find a few frameworks come up again and again. Each one takes a different approach, but all of them help you build stronger protections, manage risk, and create a culture of security across your organization. Here’s a quick look at the models most organizations use to guide their cybersecurity efforts.
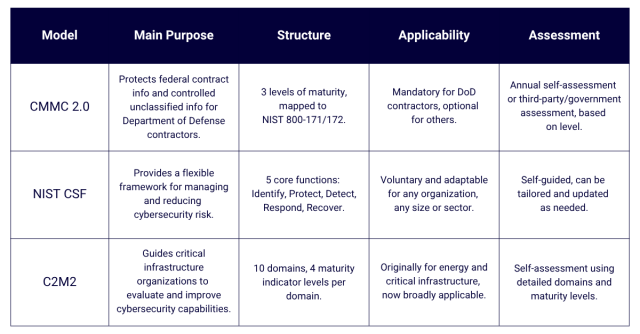
CMMC 2.0 (Cybersecurity Maturity Model Certification)
CMMC 2.0 was created by the Department of Defense to safeguard federal contract information (FCI) and controlled unclassified information (CUI). It uses a three-level structure:
- Level 1 covers basic FCI protection, with 15 controls and an annual self-assessment.
- Level 2 offers broader protection for CUI, aligning with NIST SP 800-171 and requiring third-party assessments every three years.
- Level 3 adds enhanced CUI protection, including additional NIST SP 800-172 controls and a government-led assessment every three years.
CMMC 2.0 is a must if you’re in the DoD supply chain and want a structured route to compliance.
NIST Cybersecurity Framework (NIST CSF)
The NIST Cybersecurity Framework (CSF) is a flexible, voluntary model built around five core functions: Identify, Protect, Detect, Respond, and Recover. It’s designed for organizations of all sizes looking for a risk-based foundation. What makes NIST CSF special is its adaptability. You can use its Core, Implementation Tiers, and Profiles to benchmark where you are and plan where you want to go. It's voluntary, risk-based, and doesn't lock you into a one-size-fits-all approach.
Many organizations start with NIST CSF because it gives you a solid foundation without being overly prescriptive about how you get there.
C2M2 (Cybersecurity Capability Maturity Model)
The Cybersecurity Capability Maturity Model (C2M2) was developed by the Department of Energy, mainly for the energy sector, though it’s useful beyond that. It includes over 350 practices across 10 domains and uses four Maturity Indicator Levels (MIL 0–3) per domain.
C2M2 offers a very detailed and domain-specific roadmap, helping organizations understand where they stand today and how to improve in areas like governance, asset management, and incident response.
Comparing cybersecurity maturity models
Choosing between these models isn't about finding the "best" one; it's about finding the right fit for your situation. Here's how they stack up:
Which framework is right for your organization?
Choosing the best cybersecurity maturity model comes down to your organization’s unique needs:
- Choose CMMC 2.0 if you're required to work with the Department of Defense or want a structured, compliance-driven approach with clear requirements.
- Choose NIST CSF if you want flexibility to adapt the framework to your specific needs, industry, and risk profile. It's the go-to choice for most organizations starting their maturity assessment.
- Choose C2M2 if you manage critical infrastructure, especially in the energy sector, and need a detailed, domain-based assessment that covers operational technology as well as IT.
How to implement a cybersecurity maturity model
Rolling out a cybersecurity maturity model can sound technical, but it’s really about giving your business a practical path forward. Here’s how you can move from guessing to knowing, one step at a time.
Step 1: Conduct a cybersecurity maturity assessment
Before you can improve anything, you need to know where you stand. This means taking an honest look at your current security posture.
Start by choosing your framework and conducting a baseline assessment. You can do this internally using the model's self-assessment tools or bring in an external partner for an objective perspective. The goal is to identify your current maturity level across all domains and spot the biggest gaps.
Don't skip this step or rush through it. A thorough assessment gives you the foundation for everything that comes next.
Step 2: Define objectives and compliance requirements
Now that you know where you are, get clear about where you want to go. Are you trying to meet specific compliance requirements like CMMC certification? Are you focused on protecting customer data? Do you need to build trust with business partners?
Your objectives will drive your priorities. If compliance is non-negotiable, that shapes your roadmap. If you're more focused on business risk, you might prioritize different areas first.
Step 3: Build a roadmap and assign responsibilities
This is where strategy becomes action. Take your assessment results and objectives, then create a realistic plan for closing gaps and improving your maturity.
Break your plan into phases, starting with quick wins and critical vulnerabilities. Assign clear ownership for each initiative: who's responsible for policy updates? Who's leading the incident response improvements? Who's managing vendor assessments?
Make sure your timeline is realistic. Security improvements take time, and trying to do everything at once usually means nothing is done well.
Step 4: Execute and monitor progress
Start implementing your plan, but don't just set it and forget it. Schedule regular check-ins to review progress, address roadblocks, and adjust your approach if needed.
Consider conducting follow-up maturity assessments quarterly or semi-annually to track your progress. Share updates with leadership and celebrate wins along the way. This keeps momentum going and shows the value of your security investments.
How to improve cybersecurity maturity with Flexential
Every organization’s cybersecurity journey looks a little different, but Flexential has built a proven cybersecurity services model to help you see where you stand and know exactly how to keep moving forward. The Flexential Cybersecurity Maturity Model is designed to give you a clear understanding of your current maturity, help you spot gaps, and set priorities for the most impactful next steps.
Five levels of cybersecurity maturity:
The Flexential model guides you through five distinct stages:
- Beginning
- Developing
- Advancing
- Effective
- Proactive
As you move through these levels, you gain not just stronger defenses but more confidence in your organization’s ability to protect itself and respond quickly if something goes wrong.
Ten key elements:
A mature cybersecurity program at Flexential covers these ten essential elements of a cybersecurity program:
- Roles: Clear responsibilities and accountability
- Risk management: Understanding and managing your risk exposure
- Vulnerability management: Finding and fixing security weaknesses
- IT security posture: Strong technical controls and monitoring
- Compliance: Meeting regulatory and contractual requirements
- Penetration testing: Regular testing of your defenses
- Privacy: Protecting sensitive data appropriately
- Incident response: Quick, effective response to security incidents
- Governance: Strategic oversight and decision-making
- Observability: Visibility into your security environment
Each element combines people, processes, and technology to help you build a strong, defense-in-depth approach that reduces risk and prepares your business for new threats. The Flexential team works with you to quickly identify your current state, choose the right next steps, and keep you progressing at a pace that matches your goals.
To see the full model and explore how it works, download the Accelerate Your Cybersecurity Maturity Journey white paper.
Case study: Connectbase supercharges DevOps and security
Connectbase needed to scale their operations quickly while maintaining high performance and reliability. Here's how our professional services team helped them improve their security maturity:
- Rapid delivery: We provided an Azure-focused DevOps team, including a lead engineer, two supporting engineers, and a dedicated Scrum Master.
- Seamless integration: Our experts worked alongside Connectbase’s internal team, joining sprint planning and stand-ups to provide ongoing guidance and support.
- Tangible results: Connectbase gained the expertise they needed without growing their headcount. They boosted performance, reduced time to market, and improved how their team worked, thanks to DevOps practices, not just infrastructure.
“Flexential is a part of our transformation story. Our team is performing better now with fewer people in a more cost-efficient way, and that’s a tribute to the commercial model Flexential brings along with their experience and wisdom.”
—Trey Willis, CTO, Connectbase
Key takeaways
Cybersecurity maturity models matter more than ever. They give you a practical way to see where your defenses stand and guide you in making improvements that really count. By following a maturity model, you can set priorities, measure progress, and focus your efforts where they’ll have the biggest impact.
Flexential is ready to support you at every step. Whether you’re starting with an assessment or need a full roadmap, our team partners with yours to build a strong cybersecurity strategy and keep your business protected.
Want to go further?
Explore our Cybersecurity Maturity resources or contact our team to get expert advice tailored to your organization’s needs.
FAQs about cybersecurity maturity models
What is a maturity model in cybersecurity?
A cybersecurity maturity model is a framework that helps organizations measure how strong their security practices are. It breaks down cybersecurity into levels or stages, so you can see where you stand now and what you can do to improve.
What is the best maturity model for cybersecurity?
There’s no one-size-fits-all answer; the best model depends on your industry, goals, and compliance needs. Many organizations use the NIST Cybersecurity Framework for its flexibility, while those in the Department of Defense supply chain must follow CMMC. The C2M2 model is great for critical infrastructure and energy sectors.
How does the Cybersecurity Maturity Model benefit organizations?
Maturity models help you spot gaps, set priorities, and make sure your resources are used where they matter most. They give your team a clear roadmap, help you meet compliance goals, and build confidence that your organization can handle whatever comes next.
What are the different levels of maturity in the Cybersecurity Maturity Model?
Levels vary by model, but generally range from basic (ad-hoc or reactive security) to advanced (proactive, optimized, and continuously improving). For example, the Flexential model has five levels: Beginning, Developing, Advancing, Effective, and Proactive.
What steps should be taken to progress through the levels of the Cybersecurity Maturity Model?
Set clear objectives, build a practical roadmap, and assign roles so everyone knows their part. Focus first on closing critical gaps, then continue to monitor and improve your program over time. Regular check-ins and updates help you keep moving forward.
What’s the difference between CMMC and NIST CSF?
CMMC is designed for Department of Defense contractors and has specific compliance requirements and levels. NIST CSF is a flexible, voluntary framework that can be used by any organization, in any industry, to guide and measure cybersecurity practices.
How often should maturity assessments be conducted?
At a minimum, conduct a maturity assessment once a year or whenever you experience major changes like new regulations, technology rollouts, or organizational growth. Regular assessments keep your program current and help you catch new risks early.
Can small businesses benefit from these frameworks?
Absolutely. Maturity models aren’t just for large enterprises. Small businesses can use these frameworks to prioritize their efforts, build stronger security habits, and meet customer or regulatory expectations, without wasting resources.